Note:
This topic has been translated from a Chinese forum by GPT and might contain errors.Original topic: 使用tiup 部署完了,应等保修改了 ssh 端口,还需要我配合做什么吗?
As the topic suggests, could you please provide some guidance?
Note:
This topic has been translated from a Chinese forum by GPT and might contain errors.Original topic: 使用tiup 部署完了,应等保修改了 ssh 端口,还需要我配合做什么吗?
As the topic suggests, could you please provide some guidance?
tiup cluster edit-config
Then modify here and it will work.
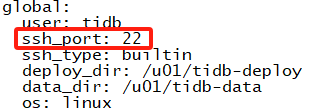
When installing, you shouldn’t use port 22, so you don’t need to modify it.
The cluster should be restarted after the modification, right?
After passing the security review, change it back to port 22.
If it’s not high-risk, there’s no need for rectification. I suggest you get someone who specializes in compliance. Changing ports is purely self-deception and doesn’t significantly improve security.
There’s no need. When you execute the command, it will execute the command through the new interface.
![]() Does this modification not require a reload? I thought all edit-config changes needed a reload to take effect~
Does this modification not require a reload? I thought all edit-config changes needed a reload to take effect~
Who should you reload for key configurations, the entire cluster? It seems like this mainly affects the tiup command…
![]() That’s true, TiUP is used to manage the cluster, so it doesn’t need to reload itself.
That’s true, TiUP is used to manage the cluster, so it doesn’t need to reload itself.
You probably need the reload command. The edit-config is just like modifying the configuration; to make the configuration take effect, you still need to load the configuration.
Using tiup to maintain the cluster also mentions the need to reload: TiUP 常见运维操作 | PingCAP 文档中心
It is recommended to use a testing environment for classified protection evaluation (as clearly supported in the classified protection documents). Do not mess around in the production environment.
From this perspective, the entire cluster really needs to be reloaded because I found that all the components below are configured with the ssh_port parameter. Why is it that even though it’s configured globally, it still needs to be configured below…
Yes, it’s somewhat similar to nginx; you need to reload the configuration for the changes to take effect.
There is no conflict. If a node does not declare a configuration, the global configuration takes precedence. If both the node and the global configuration are declared, the node configuration takes precedence.
What level of security protection is it? Messing around for nothing! If it’s internal, just handle it.
The compliance is something the customer handles themselves, so we can’t really comment on it.
This port is also used for password-free access between various components within the cluster (default tidb user, if you want to change the user, you need to adjust it in the same way). Therefore, after modification, you need to reload and distribute it to all components and update.