Note:
This topic has been translated from a Chinese forum by GPT and might contain errors.
Original topic: tidb 如何开启have_openssl、have_ssl、ssl_cipher
【TiDB Usage Environment】Production Environment
【TiDB Version】6.1.4
【Encountered Problem: Problem Phenomenon and Impact】
Security agency detection requires enabling have_openssl, have_ssl, ssl_cipher, otherwise, there are three high-risk vulnerabilities. Please help…
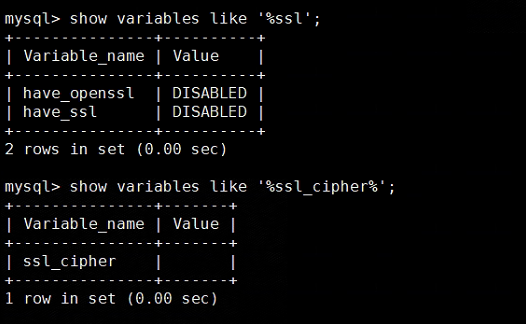
To enable SSL in TiDB, modify the enable_tls system parameter to true. These two variables should not be changed; they are read-only variables made for MySQL compatibility.
How to enable it? Is there an official document?
After modifying the corresponding parameters with tiup cluster edit-config <cluster-name>, reload the cluster to take effect.
Thanks a lot, I’ll give it a try.
If this is not enabled, it is considered a medium-risk vulnerability that can be fixed or not. Which security assessment are you referring to that considers it high-risk?
The link to the image you provided is broken or inaccessible. Please provide the text you need translated.
Enabling this means that the client connecting to the database and all internal components of the database need to use encrypted connections, which is quite troublesome.
It’s not about changing the database parameters, it’s about changing the node configuration.
After making this change, it cannot be saved. What should I do?
According to your documentation, TLS has already been enabled, but when logging into the database, these two values are still in the off state.
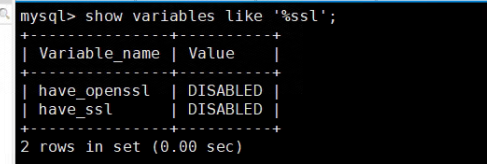
This is the 6.1 documentation. Normally, it should be enabled. How about finding an opportunity to restart and check?
I have already restarted it, but it doesn’t work.
I haven’t checked this parameter separately. If restarting the cluster doesn’t work, then it seems we can only explain that TiDB’s parameters are just compatible with MySQL but actually ineffective. 
I have done these two upgrades on Oracle before.
Has it been resolved? You need to add the ssl-ca, ssl-cert, and ssl-key configurations in the db configuration file, change the user connection method to SSL, and then log in.
Based on the documentation description, it should be read-only and requires server settings. It is not supported to set it in the cluster.
Could you provide more specific steps?

