Note:
This topic has been translated from a Chinese forum by GPT and might contain errors.
Original topic: Tidb的静态加密,完全本地存储,该如何做?
In the document mentioned, it states that you can choose to use AWS KMS (Key Management Service) for cloud or on-premises deployment, and you can also specify storing the key in plaintext in a file. How can AWS KMS be deployed locally? Are there any open-source software options? Can it completely replace AWS KMS and be deployed locally? Alternatively, if using AWS services, does network jitter affect the service?
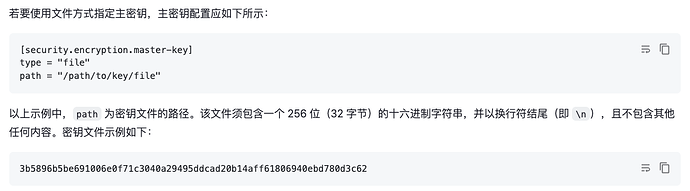
Support providing the master key in the form of a local file, so static encryption will not rely on KMS.
There are plans to provide a local key management service, currently collecting requirements.
Does this local key method support K8s deployment?
Mount a storage and then mount it into each TiKV image?
This can be done by providing the key in the form of a file, that is, writing the key to a file and allowing all TiKV nodes to access this key file. The key file path should be consistent in each TiKV node.
Minio has an open-source KMS implementation, but I haven’t used it myself, so it’s hard to judge how different it is from AWS’s interface and whether it’s compatible.
KES is a distributed key management server that scales horizontally. It can either be run as an edge server close to the applications, reducing latency to and load on a central key management system (KMS), or as a central key management server. Edge servers are self-contained stateless nodes close to the application that can be scaled up/down automatically. Central KES servers or clusters are stateful systems that store and manage cryptographic keys and secrets securely.
Minio’s object storage needs no introduction; its interface is quite similar to AWS’s. If you’re willing to tinker with this KMS, you can give it a try. If it works, writing an article about your experience would be a contribution to the community. 
Provide AWS KMS write parameters.
Waiting for the best answer to appear in the thread.
The local key management service (in addition to plaintext key files) will consider compatibility with MySQL’s design. You can refer to MySQL’s related documentation: https://dev.mysql.com/doc/refman/8.0/en/keyring.html
If you have more requirements, you can raise them here, and I will collect them. Thank you.